Download Zeus Virus
Is a global technology leader that designs, develops and supplies semiconductor and infrastructure software solutions. Clampi (also known as Ligats, llomo, or Rscan) is a strain of computer malware which infects Windows computers. More specifically, as a man-in-the-browser banking trojan designed to transmit financial and personal information from a compromised computer to a third party for potential financial gain as well as report on computer configuration, communicate with a central server, and act as.
Zeus, ZeuS, or Zbot is a Trojan horsemalware package that runs on versions of Microsoft Windows. While it can be used to carry out many malicious and criminal tasks, it is often used to steal banking information by man-in-the-browserkeystroke logging and form grabbing. It is also used to install the CryptoLockerransomware.[1] Zeus is spread mainly through drive-by downloads and phishing schemes. First identified in July 2007 when it was used to steal information from the United States Department of Transportation,[2] it became more widespread in March 2009. In June 2009 security company Prevx discovered that Zeus had compromised over 74,000 FTP accounts on websites of such companies as the Bank of America, NASA, Monster.com, ABC, Oracle, Play.com, Cisco, Amazon, and BusinessWeek.[3] Similarly to Koobface, Zeus has also been used to trick victims of technical support scams into giving the scam artists money through pop-up messages that claim the user has a virus, when in reality they might have no viruses at all. The scammers may use programs such as Command prompt or Event viewer to make the user believe that their computer is infected.[4]
Detection
Zeus is very difficult to detect even with up-to-date antivirus and other security software as it hides itself using stealth techniques.[5] It is considered that this is the primary reason why the Zeus malware has become the largest botnet on the Internet: Damballa estimated that the malware infected 3.6 million PCs in the U.S. in 2009.[6] Security experts are advising that businesses continue to offer training to users to teach them to not to click on hostile or suspicious links in emails or Web sites, and to keep antivirus protection up to date. Antivirus software does not claim to reliably prevent infection; for example Symantec's Browser Protection says that it can prevent 'some infection attempts'.[7]
FBI crackdown
In October 2010 the US FBI announced that hackers in Eastern Europe had managed to infect computers around the world using Zeus.[8] The virus was distributed in an e-mail, and when targeted individuals at businesses and municipalities opened the e-mail, the trojan software installed itself on the victimized computer, secretly capturing passwords, account numbers, and other data used to log into online banking accounts.
The hackers then used this information to take over the victims’ bank accounts and make unauthorized transfers of thousands of dollars at a time, often routing the funds to other accounts controlled by a network of money mules, paid a commission. Many of the U.S. money mules were recruited from overseas. They created bank accounts using fake documents and false names. Once the money was in the accounts, the mules would either wire it back to their bosses in Eastern Europe, or withdraw it in cash and smuggle it out of the country.[9]
More than 100 people were arrested on charges of conspiracy to commit bank fraud and money laundering, over 90 in the US, and the others in the UK and Ukraine.[10] Members of the ring had stolen $70 million.
In 2013 Hamza Bendelladj, known as Bx1 online, was arrested in Thailand [11] and deported to Atlanta, Georgia, USA. Early reports said that he was the mastermind behind ZeuS. He was accused of operating SpyEye (a bot functionally similar to ZeuS) botnets, and suspected of also operating ZeuS botnets. He was charged with several counts of wire fraud and computer fraud and abuse.[12] Court papers allege that from 2009 to 2011 Bendelladj and others 'developed, marketed, and sold various versions of the SpyEye virus and component parts on the Internet and allowed cybercriminals to customize their purchases to include tailor-made methods of obtaining victims’ personal and financial information'. It was also alleged that Bendelladj advertised SpyEye on Internet forums devoted to cyber- and other crimes and operated Command and Control servers.[13] The charges in Georgia relate only to SpyEye, as a SpyEye botnet control server was based in Atlanta.
Possible retirement of creator
In late 2010, a number of Internet security vendors including McAfee and Internet Identity claimed that the creator of Zeus had said that he was retiring and had given the source code and rights to sell Zeus to his biggest competitor, the creator of the SpyEye trojan. However, those same experts warned the retirement was a ruse and expect the developer to return with new tricks.[14][15]
See also
- Gameover ZeuS, the successor to ZeuS
References
What Is The Zeus Virus
- ^Abrams, Lawrence. 'CryptoLocker Ransomware Information Guide and FAQ'. Bleeping Computer. Retrieved 25 October 2013.
- ^Jim Finkle (17 July 2007). 'Hackers steal U.S. government, corporate data from PCs'. Reuters. Retrieved 17 November 2009.
- ^Steve Ragan (29 June 2009). 'ZBot data dump discovered with over 74,000 FTP credentials'. The Tech Herald. Archived from the original on 25 November 2009. Retrieved 17 November 2009.
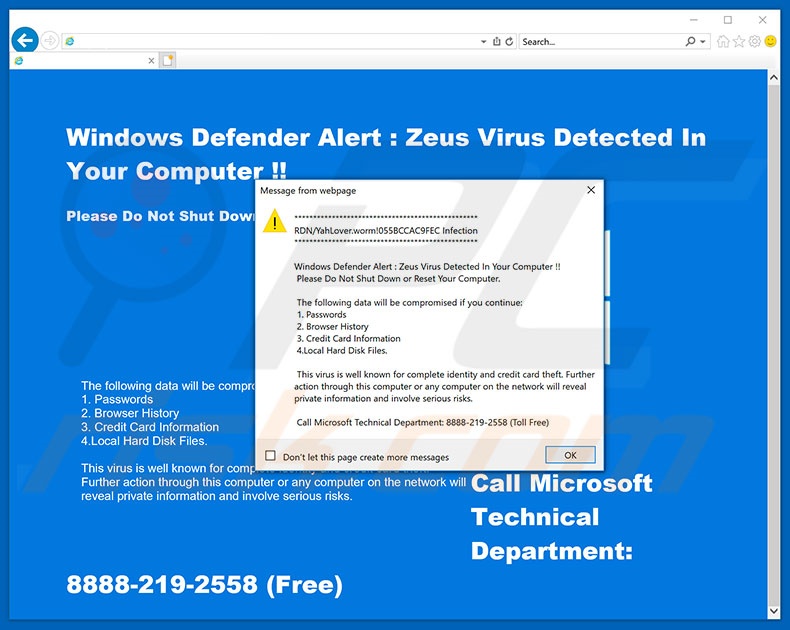
- ^'How to Recognize a Fake Virus Warning'. Retrieved 28 July 2016.
- ^'ZeuS Banking Trojan Report'. Dell SecuWorks. Retrieved 2 March 2016.
- ^'The Hunt for the Financial Industry's Most-Wanted Hacker'. Bloomberg Business. Retrieved 2 March 2016.
- ^'Trojan.Zbot'. Symantec. Retrieved 19 February 2010.
- ^'Cyber Banking Fraud'. The Federal Bureau of Investigation. Retrieved 2 March 2016.
- ^FBI (1 October 2010). 'CYBER BANKING FRAUD Global Partnerships Lead to Major Arrests'. Archived from the original on 3 October 2010. Retrieved 2 October 2010.
- ^BBC (1 October 2010). 'More than 100 arrests, as FBI uncovers cyber crime ring'. BBC News. Retrieved 2 October 2010.
- ^Al Jazeera (21 September 2015). 'Hamza Bendelladj: Is the Algerian hacker a hero?'. AJE News. Retrieved 21 March 2016.
- ^Zetter, Kim. 'Alleged 'SpyEye' Botmaster Ends Up in America, Handcuffs, Kim Zetter, Wired, 3 May 2013'. Wired.com. Retrieved 30 January 2014.
- ^'Alleged 'SpyEye' mastermind extradited to US, Lisa Vaas, 7 May 2013, Sophos nakedsecurity'. Nakedsecurity.sophos.com. 7 May 2013. Retrieved 30 January 2014.
- ^Diane Bartz (29 October 2010). 'Top hacker 'retires'; experts brace for his return'. Reuters. Retrieved 16 December 2010.
- ^Internet Identity (6 December 2010). 'Growth in Social Networking, Mobile and Infrastructure Attacks Threaten Corporate Security in 2011'. Yahoo! Finance. Retrieved 16 December 2010.
External links
| Wikinews has related news: |
- 'Measuring the in-the-wild effectiveness of Antivirus against Zeus' Study by Internet security firm Trusteer.
- 'A summary of the ZeuS Bot' A summary of ZeuS as a Trojan and Botnet, plus vector of attacks.
- 'The Kneber BotNet' by Alex Cox NetWitness Whitepaper on the Kneber botnet.
- 'België legt fraude met onlinebankieren bloot' Dutch news article about a banking trojan
- 'Indications in affected systems' Files and registry keys created by different versions of Zeus Trojan.
- Zeus, le dieu des virus contre les banques(in French)
- Botnet Bust - SpyEye Malware Mastermind Pleads Guilty, FBI
July 24, 2020
Try Norton 360 FREE 30-Day Trial* - Includes Norton Secure VPN
30 days of FREE* comprehensive antivirus, device security and online privacy with Norton Secure VPN.
*Terms Apply
A Trojan horse, or Trojan, is a type of malicious code or software that looks legitimate but can take control of your computer. A Trojan is designed to damage, disrupt, steal, or in general inflict some other harmful action on your data or network.
A Trojan acts like a bona fide application or file to trick you. It seeks to deceive you into loading and executing the malware on your device. Once installed, a Trojan can perform the action it was designed for.
A Trojan is sometimes called a Trojan virus or a Trojan horse virus, but that’s a misnomer. Viruses can execute and replicate themselves. A Trojan cannot. A user has to execute Trojans. Even so, Trojan malware and Trojan virus are often used interchangeably.
Whether you prefer calling it Trojan malware or a Trojan virus, it’s smart to know how this infiltrator works and what you can do to keep your devices safe.
How do Trojans work?
Here’s a Trojan malware example to show how it works.
You might think you’ve received an email from someone you know and click on what looks like a legitimate attachment. But you’ve been fooled. The email is from a cybercriminal, and the file you clicked on — and downloaded and opened — has gone on to install malware on your device.
When you execute the program, the malware can spread to other files and damage your computer.
How? It varies. Trojans are designed to do different things. But you’ll probably wish they weren’t doing any of them on your device.
Common types of Trojan malware, from A to Z
Here’s a look at some of the most common types of Trojan malware, including their names and what they do on your computer:
Backdoor Trojan
This Trojan can create a “backdoor” on your computer. It lets an attacker access your computer and control it. Your data can be downloaded by a third party and stolen. Or more malware can be uploaded to your device.
Distributed Denial of Service (DDoS) attack Trojan
This Trojan performs DDoS attacks. The idea is to take down a network by flooding it with traffic. That traffic comes from your infected computer and others.
Downloader Trojan
This Trojan targets your already-infected computer. It downloads and installs new versions of malicious programs. These can include Trojans and adware.
Fake AV Trojan
This Trojan behaves like antivirus software, but demands money from you to detect and remove threats, whether they’re real or fake.
Game-thief Trojan
The losers here may be online gamers. This Trojan seeks to steal their account information.
Infostealer Trojan
As it sounds, this Trojan is after data on your infected computer.
Mailfinder Trojan
This Trojan seeks to steal the email addresses you’ve accumulated on your device.
Ransom Trojan
This Trojan seeks a ransom to undo damage it has done to your computer. This can include blocking your data or impairing your computer’s performance.
Remote Access Trojan
This Trojan can give an attacker full control over your computer via a remote network connection. Its uses include stealing your information or spying on you.
Rootkit Trojan
A rootkit aims to hide or obscure an object on your infected computer. The idea? To extend the time a malicious program runs on your device.
SMS Trojan
This type of Trojan infects your mobile device and can send and intercept text messages. Texts to premium-rate numbers can drive up your phone costs.
Trojan banker
This Trojan takes aim at your financial accounts. It’s designed to steal your account information for all the things you do online. That includes banking, credit card, and bill pay data.
Trojan IM
This Trojan targets instant messaging. It steals your logins and passwords on IM platforms.
That’s just a sample. There are a lot more.
Examples of Trojan malware attacks
Trojan malware attacks can inflict a lot of damage. At the same time, Trojans continue to evolve. Here are three examples.
- Rakhni Trojan.This malware has been around since 2013. More recently, it can deliver ransomware or a cryptojacker (allowing criminals to use your device to mine for cryptocurrency) to infected computers. “The growth in coin mining in the final months of 2017 was immense,” the 2018 Internet Security Threat Report notes. “Overall coin-mining activity increased by 34,000 percent over the course of the year.”
- ZeuS/Zbot.This banking Trojan is another oldie but baddie. ZeuS/Zbot source code was first released in 2011. It uses keystroke logging — recording your keystrokes as you log into your bank account, for instance — to steal your credentials and perhaps your account balance as well.
How Trojans impact mobile devices
Trojans aren’t problems for only laptop and desktop computers. They can also impact your mobile devices, including cell phones and tablets.
In general, a Trojan comes attached to what looks like a legitimate program. In reality, it is a fake version of the app, loaded up with malware. Cybercriminals will usually place them on unofficial and pirate app markets for unsuspecting users to download.
In addition, these apps can also steal information from your device, and generate revenue by sending premium SMS texts.
Download Zeus Virus Protection
One form of Trojan malware has targeted Android devices specifically. Called Switcher Trojan, it infects users’ devices to attack the routers on their wireless networks. The result? Cybercriminals could redirect traffic on the Wi-Fi-connected devices and use it to commit various crimes.
How to help protect against Trojans
Here are some dos and don’ts to help protect against Trojan malware. First, the dos:
- Computer security begins with installing and running an internet security suite. Run periodic diagnostic scans with your software. You can set it up so the program runs scans automatically during regular intervals.
- Update your operating system’s software as soon as updates are made available from the software company. Cybercriminals tend to exploit security holes in outdated software programs. In addition to operating system updates, you should also check for updates on other software that you use on your computer.
- Protect your accounts with complex, unique passwords. Create a unique password for each account using a complex combination of letters, numbers, and symbols.
- Keep your personal information safe with firewalls.
- Back up your files regularly. If a Trojan infects your computer, this will help you to restore your data.
- Be careful with email attachments. To help stay safe, scan an email attachment first.
A lot of things you should do come with a corresponding thing not to do — like, do be careful with email attachments and don’t click on suspicious email attachments. Here are some more don’ts.
- Don’t visit unsafe websites. Some internet security software will alert you that you’re about to visit an unsafe site, such as Norton Safe Web.
- Don’t open a link in an email unless you’re confident it comes from a legitimate source. In general, avoid opening unsolicited emails from senders you don’t know.
- Don’t download or install programs if you don’t have complete trust in the publisher.
- Don’t click on pop-up windows that promise free programs that perform useful tasks.
- Don’t ever open a link in an email unless you know exactly what it is.
Trojan war winners and losers

A final note on Trojans for history and mythology buffs.
Trojans take their name from the hollow wooden horse that the Greeks hid inside of during the Trojan War. The Trojans, thinking the horse was a gift, opened their walled city to accept it, allowing the Greeks to come out of hiding at night to attack the sleeping Trojans.
In the same way, if you’re the victim of Trojan malware, you could find yourself on the losing side. It pays to stay alert, be careful, and don’t take chances — no matter what type of devices you’re using to stay connected.
Try Norton 360 FREE 30-Day Trial* - Includes Norton Secure VPN
30 days of FREE* comprehensive antivirus, device security and online privacy with Norton Secure VPN.
*Terms Apply
Editorial note: Our articles provide educational information for you. NortonLifeLock offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about cyber safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses.
Copyright © 2021 NortonLifeLock Inc. All rights reserved. NortonLifeLock, the NortonLifeLock Logo, the Checkmark Logo, Norton, LifeLock, and the LockMan Logo are trademarks or registered trademarks of NortonLifeLock Inc. or its affiliates in the United States and other countries. Firefox is a trademark of Mozilla Foundation. Android, Google Chrome, Google Play and the Google Play logo are trademarks of Google, LLC. Mac, iPhone, iPad, Apple and the Apple logo are trademarks of Apple Inc., registered in the U.S. and other countries. App Store is a service mark of Apple Inc. Alexa and all related logos are trademarks of Amazon.com, Inc. or its affiliates. Microsoft and the Window logo are trademarks of Microsoft Corporation in the U.S. and other countries. The Android robot is reproduced or modified from work created and shared by Google and used according to terms described in the Creative Commons 3.0 Attribution License. Other names may be trademarks of their respective owners.
No one can prevent all identity theft or cybercrime. Not all products, services and features are available on all devices or operating systems. System requirement information on norton.com.
*Important Subscription, Pricing and Offer Details:
- The price quoted today may include an introductory offer. After that, your membership will automatically renew and be billed at the applicable monthly or annual renewal price found here.
- You can cancel your subscription at my.norton.com or by contacting Member Services & Support. For more details, please visit the Refund Policy.
- Your subscription may include product, service and /or protection updates and features may be added, modified or removed subject to the acceptance of the Customer Agreement.
The number of supported devices allowed under your plan are primarily for personal or household use only. Not for commercial use. If you have issues adding a device, please contact Member Services & Support.
§ Dark Web Monitoring in Norton 360 plans defaults to monitor your email address only. Please login to the portal to review if you can add additional information for monitoring purposes.